Roger Binns — Wed 07 August 2013
In a fit of madness I decided to replace the self signed SSL
certificate I use with a proper one. The self signed one I made was
good for 10 years so I didn't have to deal with renewal nonsense.
Various clients did whine a bit, but usually there was some setting to
tell them it was ok. The biggest problem with a self signed cert is
you generally can't tell the difference between it and a middleman
intercepting your connection.
SSL certificates are a curious business. Just like with the credit
rating agencies and the banking crisis, the incentives and payments
are all wrong. The certificate is analogous to an identity document
like a drivers license or a passport. Identity documents are trusted
not because of the information on them, but rather who issued them.
My British passport is only trusted around the world because the
British government is trusted as the issuer. A self signed SSL
certificate is analogous to printing your own passport saying it comes
from the Republic of You.
To get a SSL certificate you engage with a certificate authority.
They will verify your identity information to some degree, accept your
money and issue the certificate. But the people who care about your
identity are the ones connecting to your site, and they haven't been
involved in this process. The browser and operating system
manufacturers handily include a list of trusted certificate
authorities, but the way it works is that any name will be accepted
providing any of those authorities issued it!
Here is the start of the long list of trusted authorities:
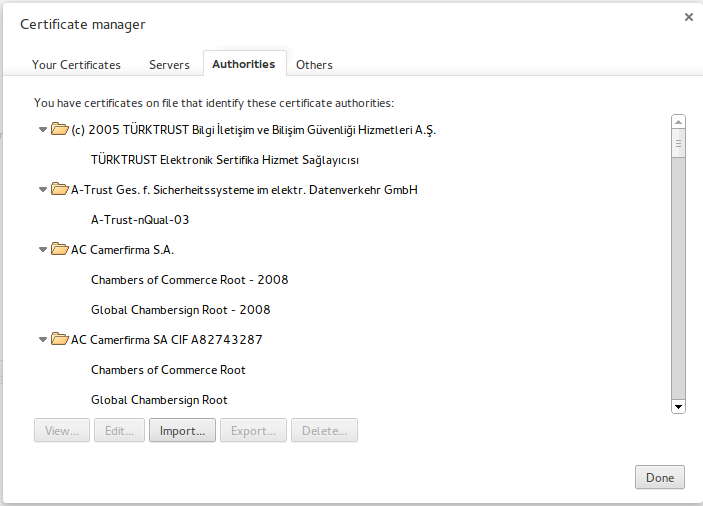
If any of those issued a certificate for my site, your browser would
trust it, or for amazon.com or microsoft.com for that matter.
For the certificate authority businesses to operate, they need to
remain in those trusted lists, but also need to make it easy to
exchange money for certificates.
Their solution is multiple "classes" - they create intermediate
certificate authorities and each of those then has different
requirements. For example a class 1 might check there is a working
email address associated with the site, while class 3 may involve
people doing strong verification including getting business documents
and making phone calls. They charge more for the latter.
But it is rather pointless. Your browser accepts class 1
certificates that cost $20 with minimal verification as well as class
3 that cost the site thousands. As an end user, you could check the
certificate for each site you visit, determine if you trust the
certificate authority, go to their web site to read up what their
statements are for that class and decide if it acceptable risk to you.
You'll also notice they'll have some legalese disclaiming any
liability, making it essentially worthless.
This is all a long winded way of saying that it doesn't really matter
who issues your certificates, there are no real assurances behind them
any way, and nobody checks. They wouldn't be too different from real
world passports printed on tissue paper that only machines ever look
at. Consequently I used the free StartSSL certificate authority.
The sign up process is annoying and tedious, largely to try to give
the appearance of value and security. New certificate in hand, I then
had to replace my self signed certificate. This was more complicated
because I also had to include the intermediary authority information.
The various applications I tried all worked perfectly, except those
from Mozilla. In the olden days they would give detailed information
about SSL issues, but it was gobbeldy gook, so naturally most users
clicked whatever they could to get them to the site as quickly as
possible. It is virtually impossible to tell the difference between
misconfiguration and security breaches. The solution was to hide all
that and try to show the minimum amount. Which leads us to today.
Thunderbird doesn't like the certificate for reasons I can't
determine. It doesn't even show an error, so it looks like it is
working but in reality it is repeatedly hanging up on the server.
When using a self signed certificate it at least puts up an error
dialog where you can say to permanently accept the certificate. In
this case the behaviour for a legitimate certificate is far worse!
Going through several arcane menu sequences you can finally make it
work, but this is ridiculous.
Firefox initially worked and then stopped. In the end I worked out
that it had OCSP
issues . I can't really tell who is to blame, and ended up having
to turn OCSP off.
Now I have a real certificate, it works providing you go nowhere near
Mozilla products, and isn't worth anything anyway. Madness indeed.
Category: misc
– Tags:
ssl, thunderbird, mozilla
